Cisco BroadWorks Vulnerabilities CVE-2021–34785 & CVE-2021–34786
Hi! Today I will talk about my last findings at Cisco products BroadSoft BroadWorks, one of Cisco products. I’ve discovered 2 CVEs at it and assigned as
- CVE-2021–34785: IDOR lead to privileges escalation “Admin account takeover”
- CVE-2021-34786: IDOR lead to delete arbitrary admin user accounts
I will not talk about the full story or something similar because I hate these useless words 😅 So let’s get started directly with the exploits and the conditions.

Content
- BroadWorks structure
- CVE-2021–34785
- CVE-2021–34786
- Weakness points
1. BroadWorks structure
At BroadWorks, we have an Admins group which have admins with write and read privileges and other admins with read-only privileges.
- Read and Write: he can modify his data and other admins' data. Also, he can add users, change system preferences, delete users, and full control the system
- Read-only: he can modify his data and delete his account. He doesn’t have any other privileges “In my case”
I’ve got the second role (Read-only) and my task is trying to escalate my privileges to have Read and Write actions.
2. CVE-2021–34785
If you tried to view system users, we have 2 users: Admin and PentestAdmin. My user is PentestAdmin which has low privileges, read his data only. User Admin have full control of the system

I tried to enumerate the admin account to know what’s allowed functions but unfortunately! There’s no allowed function to use at Admin profile, I can view the data only, but at all, I know the firstname, lastname and adminID
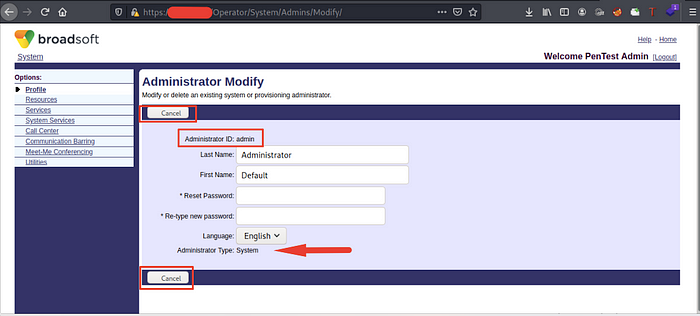
After that, I tried to enumerate my account and found that I have 2 allowed functions delete the account and change the password without asking you for your old password, weird right?!

I entered a new password and intercepted the request to know what’s the request parameters. I’ve found that we have firstname, lastname and loginid required parameters because I tried to delete loginid but unfortunately! The request failed

At all, it’s not a problem because I have privileges to read all users' data, so I know this data from the admin profile.
The final step is replacing your data with Admin data and sending the request. It returns 200 OK and to check, I tried to log in with the new password, and Bingoooo! You take over the admin account by changing his password ❤
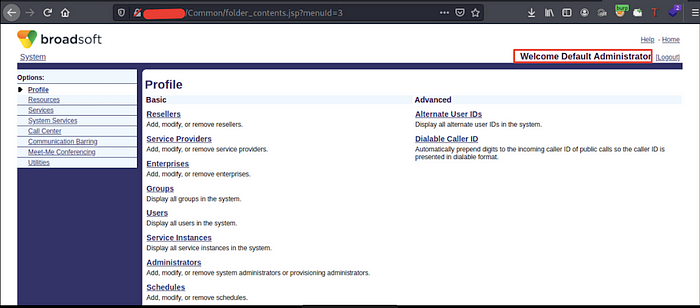

To make POC, I’ve created a new user SecmeterPOC with writing and read privileges.

After reviewing the Admin board

3. CVE-2021–34786
With the same methodology, I tried to delete my account and intercept the request.
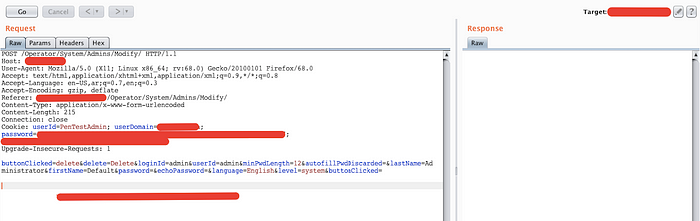
We have the same required parameters firstname/lastname/loginid and with the same exploit, just replace them with Admin account data and send the request.
What are the results? The admin account was deleted 😈

4. Weakness points
- At the change password function, it MUST ask me for the old password and if I forget it, it should ask me to contact the system administrator.
- There’s no CSRF token attached with the user session to protect the system from performing the same attack using CSRF [I have tried it and successed]
- At delete account, it MUST ask the user to enter his password or any security question


